Signum
Protect data assets from the moment they are created
Signum is an Enterprise Security and Cryptography Platform, designed to protect sensitive digital assets from the moment they are created and as long as required
Your systems and users create and exchange vast amounts of data assets, often without any protection of confidential material. Signum steps in to mitigate these issues in a cost effective manner.
How and why
Larger enteprises use various different software systems in their day-to-day business processes. Systems and their users create various documents of varying confidentiality level, and in large volume. Many of these assets lack even the most basic protection:
- Data integrity (eg. who created a document and when) is not respected and can present a significant risk to undisrupted business flow.
- Unprotected circulation of assets between users and business partners can lead to compromised secrets and creates a potential for fraud.
Upgrading large software systems with security features, as well as legacy systems, is a slow, expensive, and often unfeasible undertaking. Integrating these systems in a secure manner can present an even bigger challenge, especially with ever-increasing data exchange between business partners.
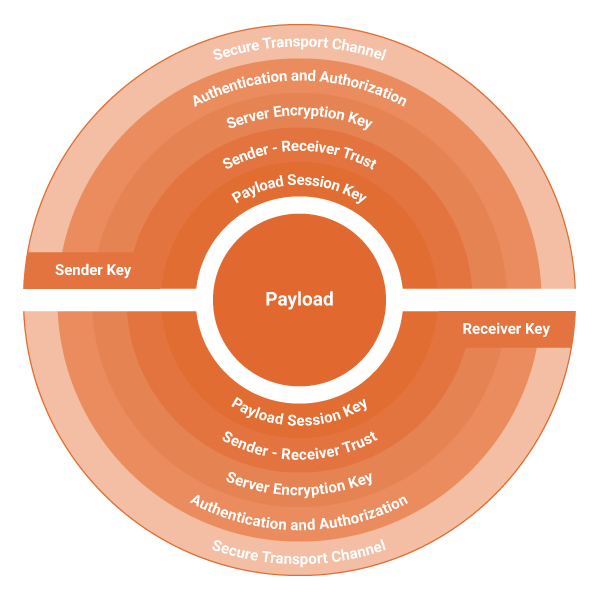
Signum acts as a security mediator between users, software systems and business partners. It allows for easy data protection and secure integration, while at the same time employing highest levels of cryptography and secure data exchange.
- By seamlessly integrating via Signum, utilizing its unified approach to data asset protection, existing systems rarely need major security hardening.
- An additional benefit is that users gain an additional level of confidence and trust, without having to know the details of protection mechanisms in place, or requiring an extensive education in IT security.
Your enterprise becomes more compliant to security standards and requirements defined by ever growing threats.